(Enterprise) Risk Management loves Configuration Management
Gartner separates Risks Management to three individual tracks from strategic to operational level.
https://www.gartner.com/en/information-technology/glossary/enterprise-risk-management
https://www.gartner.com/en/information-technology/glossary/risk-management
https://www.gartner.com/en/information-technology/glossary/security-governance
In this text “Risk Management” refers to managing risks associated to the business, starting from the chosen strategy of the organization all the way down to the possibility of someone breaking into your organization’s Active Directory.
Exciting news! Your supervisor has just tasked you with evaluating potential risks associated with business line XYZ.
Where to start?
In order to perform a Risk Analysis, you first need to understand the components of the business. Usually, any business is a set of services that the organization either
- is providing to external parties (e.g., selling coffee from kiosks in multiple locations)
- is providing for internal purposes (e.g., payroll, invoicing, IT services etc.)
- is buying from external parties (e.g., IT services, logistics)
What the organization is selling, buying, or creating for its own needs naturally depends on the industry of the organization.
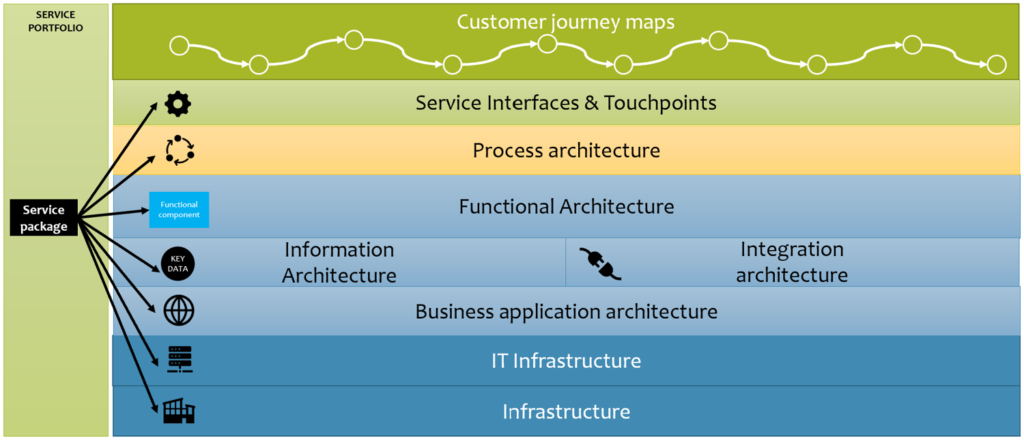
So, to understand the potential risks for the organization, the organization will need to understand the value creation in each service and how the services are interconnected. That covers
- Customer journeys and associated Service Interfaces (Phone, web pages, APIs, SMS, etc) – How do our customers and other users participate in the business activities?
- Underlying Services and contracts – What are those service touchpoints made of? Who or what entities are subscribers? What other services are used to provide services?
- Processes and the organization around them – What entities are processing the information and how?
- Functional architecture, information architecture, and integration architecture – What functional components are we using from which business applications and what information are we processing and how is it moving between the functional components and systems?
- Business applications – What information systems are we using in our processes?
- IT Infrastructure – What are the components of the information systems we are using?
- Infrastructure (physical world) – Where are all the components located in the physical world?
Why do you need all this information?
The reason is that without all these components it is impossible to evaluate the potential risks and consequential business impact in your Business Impact Analysis. You need to be able to describe the business impact of an adverse situations, such as
- Pandemic or other reason for your staff not to work from your offices or other physical locations
- Fire, water damage, or other serious physical malady at one or more of your locations
- Bankruptcy of one of your suppliers
- Loss of access to a business application (e.g., Salesforce, Dynamix, or bookkeeping software)
- <any other event your Risk Management has identified as a potential threat to your service>,
Therefore, it is absolutely mandatory to understand the components to initially figure out potential risks for each component and then assess the impact downstream from the component. In other words, you need to understand the components to answers questions such as
- What could cause a negative impact to <critical software>, what the business impact would be and how to mitigate the risk?
- What could cause the office A from being used, what the business impact would be and how to mitigate the risk?
- What could prevent us from using <low-cost offshore location> for IT services, what the business impact is and how to mitigate those risks?
- And so on…
If you are starting from nothing, this sounds like a daunting task, doesn’t it? Unfortunately, there is no shortcut to success available here and the sooner you start, the sooner you are finished.
One might think that we only have to deal with the business line XYZ here, so we don’t take the whole effort but return later. It doesn’t matter, if you only need to consider risks in smaller subset of the business or service, the needs are still the same! You cannot properly estimate the business impact of losing, e.g., VPN services without understanding which other services require VPN to function. You also cannot evaluate the risks of the VPN service without understanding who provides the service, what technology is it based on etc.
Where the organization should start
To properly assess operational risks of the business, we need a clearly defined Operating Model for (IT) Service Management, which describes tools, organization, processes, and duly maintained information. In other words, organizations need to have Service Management System (SMS) defined.
One particularly useful piece of that puzzle is Configuration Management. It describes the who, what, where, and how the Configuration Management Database (CMDB) is maintained and in what format (data model). That should answer most of the questions we had in our “Where to start” section.
Having an up-to-date information of the components of your service and the dependencies between the components and other services is crucial for being able to accurately assess risk associated with each component and the business impact if any of the risks materialize. Configuration Management makes sure you have that information available, and luckily, not only for that purpose.
Contact us if your organization needs help in
- Defining the Operating Model for Service Management (or Service Management System)
- Defining the Risk Management process(es)
- the Business Impact Analysis
- the Business Continuity and Disaster Recovery Plans
- the Configuration Management, Service Asset and Configuration Management, or CMDB
Need to know more?
Creative Service Management -handbook serves as an aid and information source for people working with service development, leadership and management. Order your copy from JustinShop.
If you need training on CMDB, Service Catalog topics or want to know the secrets of IT4IT, click here and familiarize yourself with Justin’s training offering
Checkout Creative Service Management videos on our Youtube-channel
- Intelligent Data Processing, introduces the secrets of functional architecture. The functional architecture enables the intelligent design and description of internal management systems, their functionalities, and the information processed in them.
- CMDB A-B-C: what a CMDB is and what benefits its use will bring to service organizations. In addition, the video will list the 4 most important things to consider when implementing CMDB and configuration management. English subtitles available!
If you’re not already following us on LinkedIn, you can fix it easily here: https://www.linkedin.com/company/justin-group-oy/
Julkaistu 05.04.2022
