Why information security and privacy require a working configuration management?
What is the common denominator between information security responsible and privacy responsible in the organization, regardless of their title (DPO, CIO, CISO, CDO, etc) in order to perform the job?
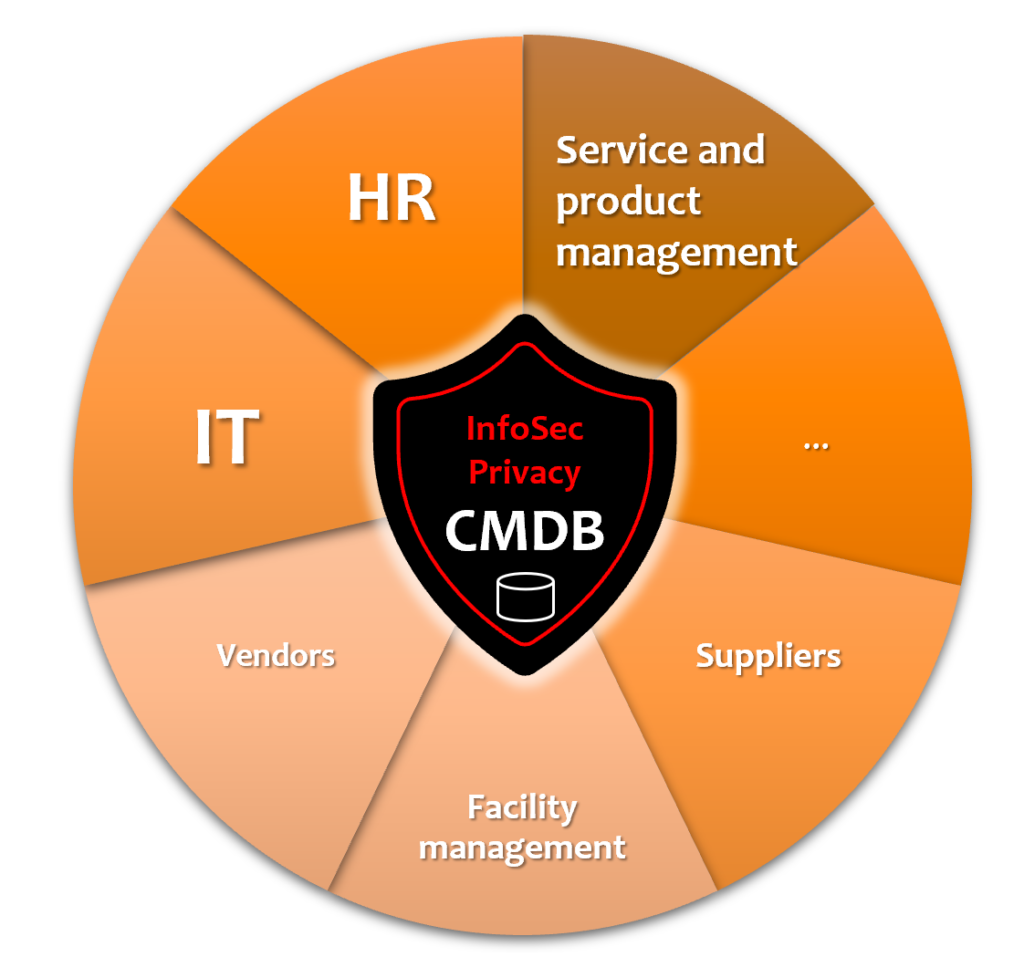
Both require an up to date Configuration Management Database (CMDB) to help them in their day-to-day work!
If you are not aware of it, you cannot protect it!
Needs: Information of Information
It is both of their responsibility to make sure that their organization is taking care of the CIA* / CIAR** responsibilities towards their internal and external stakeholders.
*Confidentiality, Integrity, Availability (from (ISC)2 CISSP material)
**Confidentiality, Integrity, Availability, Resilience (from IAPP CIPP/E and CIPM material)
In order to be able to assert that the organization is indeed taking care of the responsibilities, they must be able to gather, and keep up-to-date, information about information. This information about information is usually scattered throughout the organization’s various departments.
For example…
What kind of information is being stored? Is it personally identifiable information (PII, financial information, technical information, or something else. What attributes (e.g., person’s age, serial number of a device) are being stored. If it is personally identifiable information, how the information was gathered and what is the legitimate base we have for gathering the information.
Where the information is being stored? In addition to the geographical location of the data, the organization needs to know for example if the data is stored in a supplier’s SaaS service, organizations’ own service, or in some sort of hybrid where an external party is providing infrastructure (e.g. servers) and the organization itself governs the application layer. Where are the backups going and who is managing the backups.
How is the information protected? What kind of physical security is provided to the information. What kind of technology is being used to protect the information in flight and in rest.
Who can access the information? Who within the organization and outside the organization have access to read/write/create/delete the information. In which jurisdiction/country are the people or organizations processing the data. What kind of contracts (e.g. NDAs) we have in place with the internal and external parties. Can we perform a security audit.
How long is the information stored? Depending on the type of information (PII, financial information, technical information), the organization has rights and obligations for storing the data. On one hand there’s no limit to the time how long a name of a device can be stored, but on the other hand there are laws governing the storage of employee information and financial information.
How is the information disposed of? It is important from the information security and privacy point of view to make sure that any information that should be deleted, is deleted in such a manner that it cannot be recovered. How are the physical devices cleaned. How are we removing information from SaaS services. How long do store the backups and how are the backups cleaned.
Problems in gathering, sharing, and making sure data is up to date?
Gathering and sharing the information of information
When the organization grows, it becomes impossible for one or two persons to gather and maintain the information of information by asking around and storing the data in flat excel/word files on shared folders and similar setups. Additionally, others in the organization will also have needs for the same information.
Information gathered from IT/HR/Facility/other – departments last month will be stale by the time it is formalised into the documents.
Points of view and cross-dependencies
The organization produces services for external customers by combining their own services and products with services and products bought from external parties. Additionally, organization produces services for their internal functions and employees by combining internal and external services and products. Each service and organizational unit is interested in seeing the service information from their point of view. IT thinks they are the center of the universe, but so does HR/Sales and any other function within the organization.
As an overly simplified example: In order for Justin Group as a company to provide consulting services to its customers, Justin requires a number of internal service providers who produce services to enable the consulting services. In order to produce the internal services, Justin requires services and products from service providers outside the organizations. Additionally, the internal services enable each other’s (e.g. HR requires IT services and vice versa).
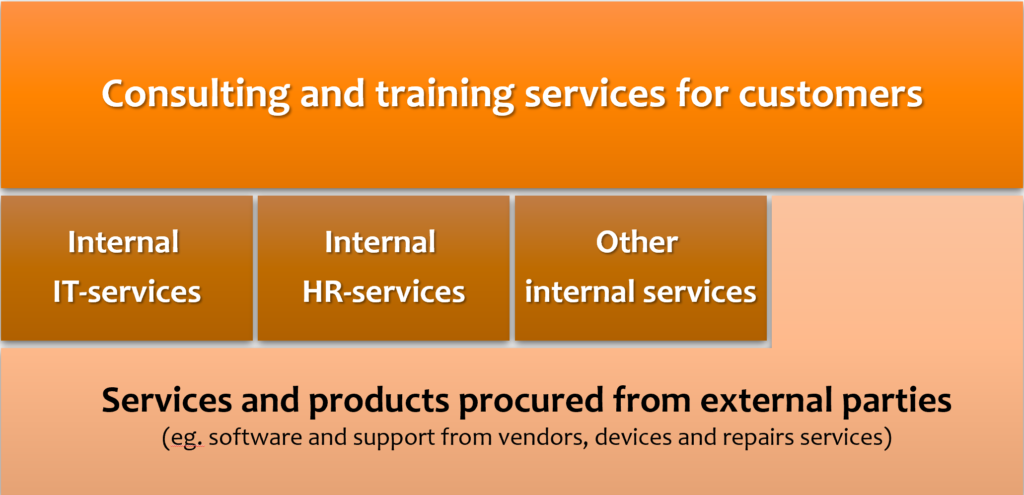
Expanding the example from one service’s point of view, but still keeping it overly simplified. I have left out for example the dependencies between IT services and cross dependencies between services from different functions.
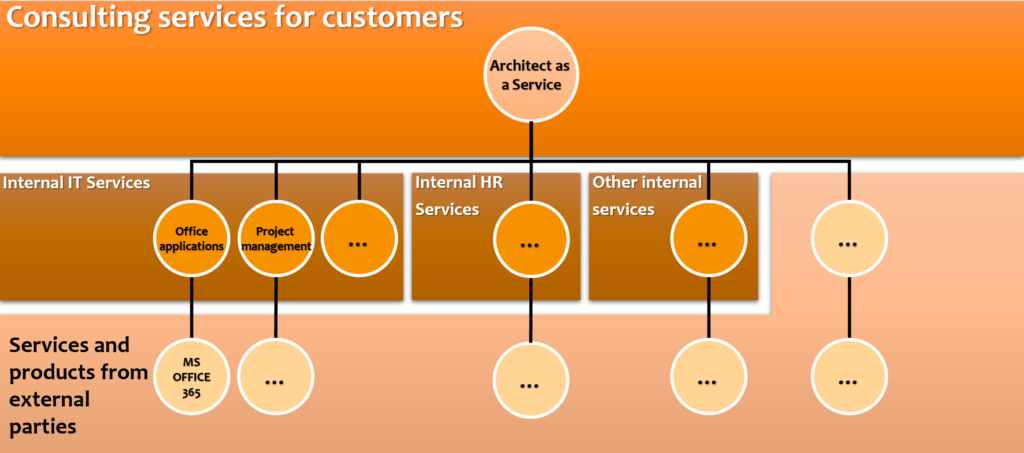
Each internal and external service is being produced with a combination of internal and external organizations, people, devices, software, and services. Each of the components should be evaluated from an information security and privacy point of view.
You can only do it if you know about the components!
Keeping the information up to date
When the information is collected, it has a bad habit of getting stale really fast unless it is continuously being kept up to date according to mutually agreed information model and stored to mutually agreed places to which correct people have access.
Solution requires agreed service information management processes and information model
In today’s world, all of the above is part of the organization’s service information management, to which modern Service Management and Service Portfolio Management systems provide a multitude of functionalities. For example: how to look at the same information from different angles and to provide access to right information for the correct people at the right time.
In order to use those functionalities to manage information management, the organization requires mutually agreed information models and processes for maintaining the information. For example:
What information is maintained and in which system? Are we storing the contract documents and names of contact persons of the services we are buying in a contract management system and the information of the technical details of the components in the service management system?
Who maintains which piece of information? Is the department or person buying the service responsible for loading the contract documents to the contract management system or will procurement do it?
How do we ascertain the up to dateness of the information? Will we have blind tests periodically? Does the selected system(s) contain functionality for auditing data?
Who is allowed or required to see what piece of information? Are the version numbers of the software confidential information due to potential vulnerabilities or should ”everyone” see the version for problem solving purposes? Will service manager see the whole contract text or just certain parts? What if the service manager is working for a supplier?
What information is integrated between systems and in which cases one system just refers to the other system? Are we for example importing workstations’ technical details from to service management system or is it enough that the information is in the MDM system such as Intune?
You can educate yourself with the above mentioned subjects at Justin Group’s trainings. We provide public trainings in addition to company specific trainings. Additionally, Justin Group’s consulting services will be able to help you with the projects and programs related to the subjects.
Read more about Justin Consulting Services
With the skills and tools you will learn from the courses, you will be able to plan your organization’s service information management processes and information model in a way that will enable the whole organization to maintain up to date CMDB which will hugely benefit everyone – including the information security and privacy responsibles!
Julkaistu 09.11.2021
